How to decrypt 802.11 ( WLAN / Wireless ) encrypted packets using Wireshark?

♣ There are different types of security in WLAN. Here we will try to decrypt all types of wireless security using Wireshark tool.
A. No Security (None/Open Security)
B. WEP-OPEN-64
C. WEP-SHARED-64
D. WEP-128(OPEN or SHARED)
E. WPA2-PSK-AES
F. WPA-PSK-TKIP
Before we get into steps of wireless packet decryption, we should know how the data packet looks like if
♦a♦ Frame is encrypted [B, C, D, E, F].
From below screenshot we can see encrypted wireless data frame.

There are two places where we should look into to understand an encrypted frame.
♦ Wireless data frame shows as Data or QoS Data [WMM enabled]
♦ There is no other layers [IP, Transport, Application] are visible in frame details. This means, all those layers are encoded inside wireless data.
If we are able to decrypt this frame then we can see the actual data.
♦b♦ Frame is decrypted or None/Open security [A].
Below is the decrypted frame or no security is configured.

In this frame we get idea of what is the actual data (Here ICMP) instead of just QoS Data.
Now we have understood the differences between encrypted and decrypted packet, let’s see the steps to decrypt wireless frame with different security.
♣ A. No Security (None/Open Security):
If no security is configured in AP then the communication between client and AP is visible in Wireshark.
Here is the screenshot for no security data frame.

♣ B. WEP-OPEN-64:
♦ WEP-OPEN-64 Encrypted frame screenshot:

♦ How to decrypt this frame?
Let’s follow the screenshots to understand the steps
[Go to Edit-> Preferences -> Protocols -> IEEE 802.11 -> Enable Decryption and go inside Edit -> Click on + sign and add WEP keys -> Save all and come back to original Wireshark window]
a.
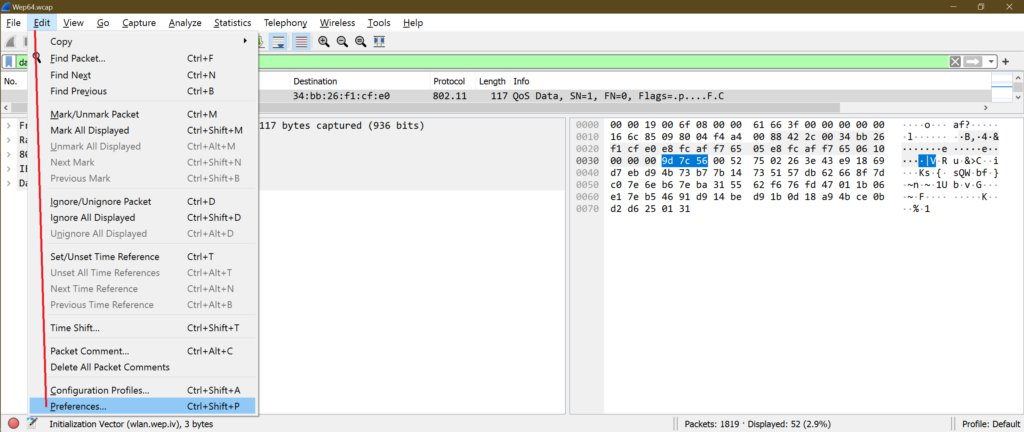
b.

c.

d.

e.

f.
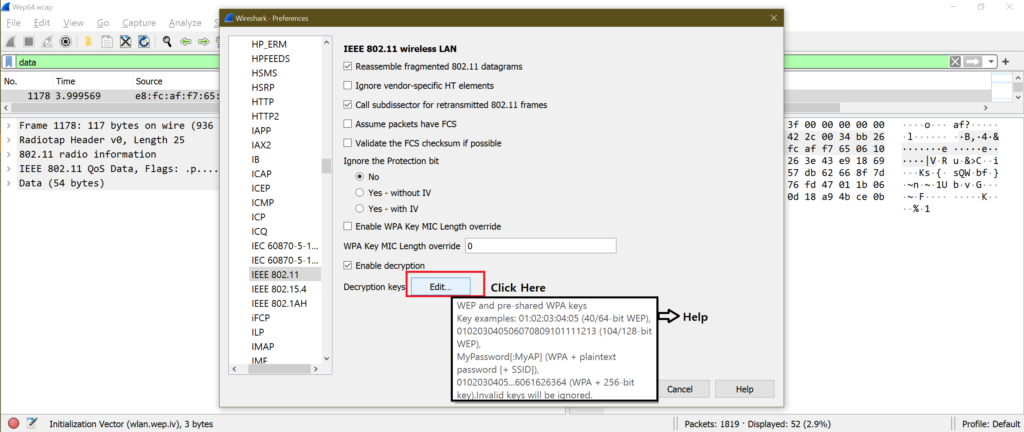
g.

h.
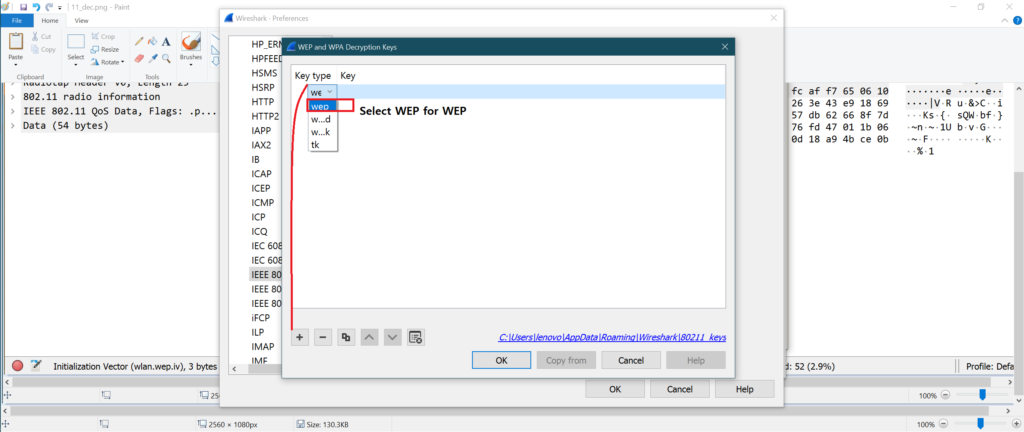
i.

j.

♦ Frame after decryption:

Note:
On Wireshark version ex: 3.4.2, there is a direct option to open step “h”.
Follow below screenshots for steps:


♣ C. WEP-SHARED-64:
The method is same as “B. WEP-OPEN-64”.
♦ WEP-SHARED-64 Encrypted frame:
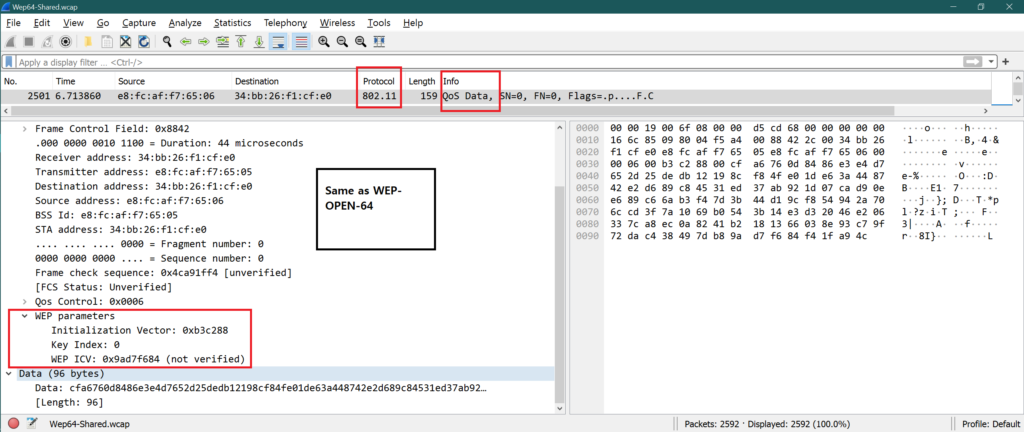
Decrypted frame:

♣ D. WEP-128(OPEN or SHARED):
♦ WEP-128 Encrypted frame:
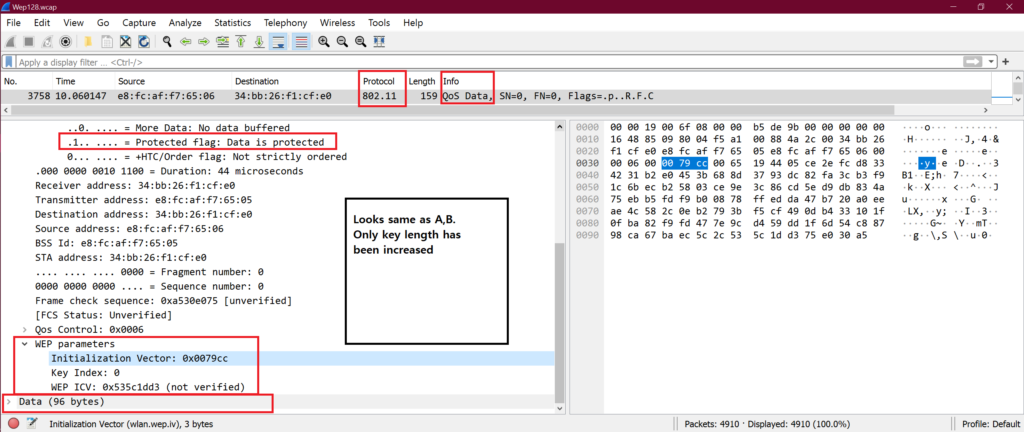
♦ How to decrypt WEP-128 encrypted frame?
Open the window showed in step “h” and follow below screenshot for steps.

♣ Decrypted frame:

Here only WEP key length is more than A, B.
♣ E. WPA2-PSK-AES:
♦ WPA2-AES Encrypted frame:

♦ WPA2-CCMP Decryption steps:
Open the window showed in step “h” and follow below screenshot for steps.

♦ Decrypted frame:

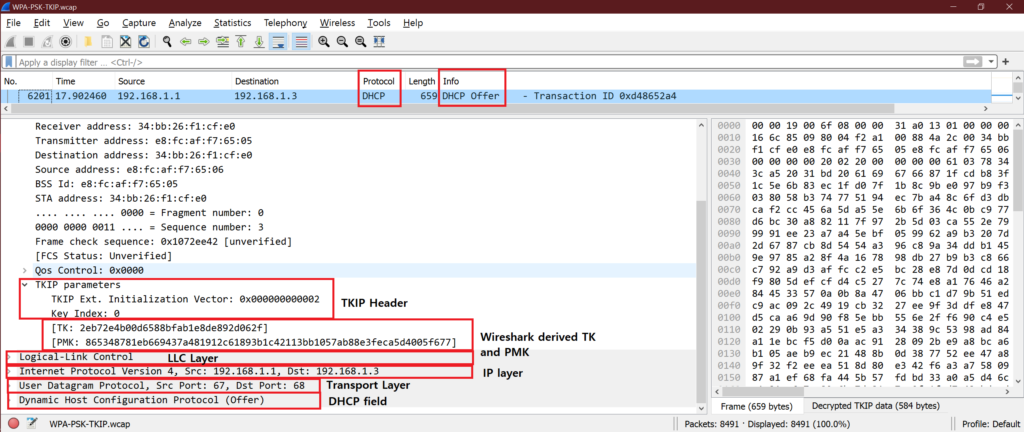
♣ F. WPA-PSK-TKIP:
♦ WPA-TKIP encrypted frame:

♦ How to decrypt WPA-TKIP frame:
Steps are exactly same as WPA-PSK-AES.
♦ Decrypted frame:
♣ Extra information:
♦ How to use “WPA-PSK” from Wireshark decryption windows?
To do this we need to generate 256bit PSK. Use below link to generate the key.

Follow below screenshot to see the steps:

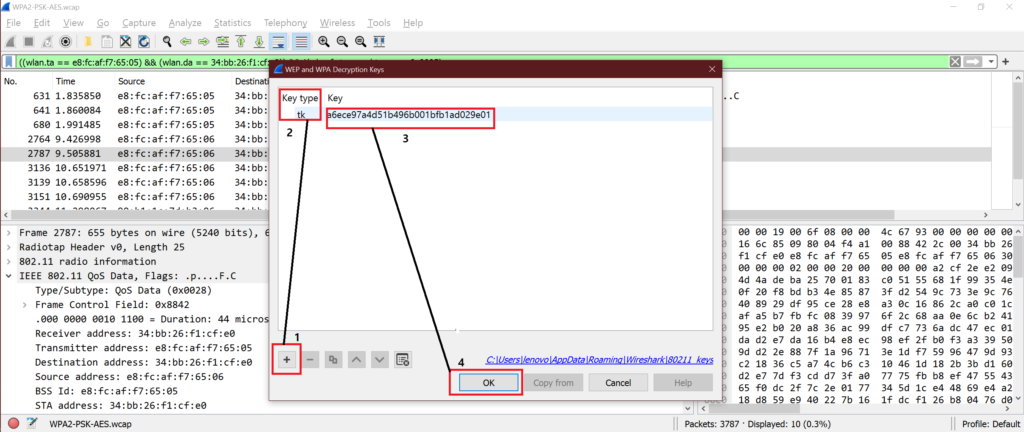
♦ How to “TK” from Wireshark decryption windows?
If we have “TK (Temporal Key)” then we can select TK option from drop down and decrypt WPA/WPA2 frames.
In our example, we have got TK as “a6ece97a4d51b496b001bfb1ad029e01” from any data packet for WPA2-PSK security decryption.

Copy the TK from here and use it in Wireshark decryption window like below.
♣ Common errors:
♦ After filling password or key and SSID of AP, the data packets are not getting decrypted. The possible reasons are
◘ Password or entered key is wrong.
◘ WPA2/WPA decryption works without filling SSID also as Wireshark takes last known SSID automatically. But it does not work always. So it’s better to put SSID AP.
◘ Capture file does not contain any of the packets from below list.
♠ Authentication
♠ Associations Request
♠ Association Response
♠ 4 or 6 EAPOL packets.
♦ If we are sure that all EAPOL packets are there in capture but we do not see EAPOL packets as EAPOL under protocol. EAPOL frames are shown as “802.11” under protocol column. The possible reasons are
◘ Something went wrong with Wireshark settings we might have done recently. Do check that.
◘ Uninstall Wireshark and install Wireshark again with “Remove my settings” option is ticked.
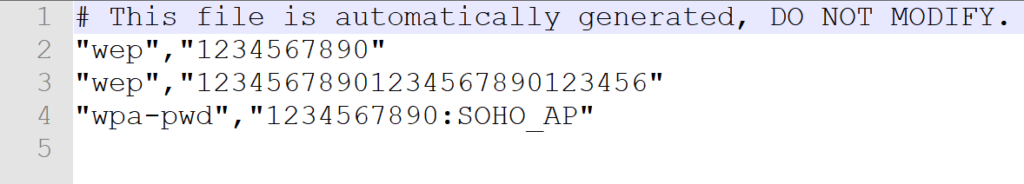
♣ Wireshark password file:
We have seen one file path in step “g”. This is the text file to store security information and password for Wireshark.
Its looks like this
♣ Conclusion:
Now we know how to decrypt all basic 802.11 security types frame with different methods. This helps us debugging any WLAN issue while testing.
Keep in mind that different Wireshark version has different style of taking input for decryption windows but all are quite simple and straight forward to understand. We have used 3.4.2 version for the article.
♥♥ you have any doubts or query please let me know in comment section or send mail at feedback@wifisharks.com.♥♥

Anki
Thanks for your time.it is really helpful for many wifi engineers.
Alden Labree
Good site you have got here.. It’s difficult to find excellent writing like yours nowadays. I honestly appreciate individuals like you! Take care!!