Basic understanding of ARP, DHCP, TCP connection and Teardown through Wireshark

♣ Introduction:
Here are we are going learn about basic of Address Resolution Protocol (ARP), Dynamic Host Configuration Protocol (DHCP), Transmission Control Protocol (TCP) connection and TCP teardown. Wireshark protocol analyzer will be used to show the packet exchanges for these protocols.
♣ Load Capture in Wireshark:
Wireshark is open source free networking tool. It can be downloaded for any operating system. After it’s installed, here is the first screen of Wireshark.

To load any capture, go to Edit->Open and select the required capture to be displayed into Wireshark.

Once any capture is loaded it will look like this.

Now let’s understand some protocols and see packets into Wireshark.
♣ ARP:
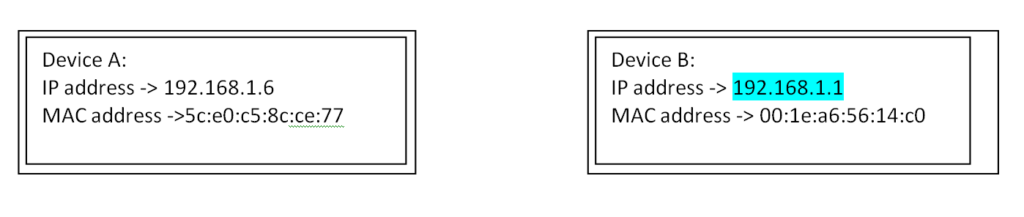
ARP protocol is used to get the MAC address of another device when you know the IP address of the another device. Let’s see below diagram to understand in simple way.
Suppose device A knows the IP address of device B but does not know MAC address of device B. What should device A do? Here are the steps.

ARP Request: Who has 192.168.1.2 tell me (A)? This is a broadcast packet————————————————————>
<————————————————————————-ARP Reply: I (B) have 192.168.1.2 and my MAC is 6C-E0-C5-8C-E0-77
So there should be two packets exchanges if someone has the requested IP in ARP request.
Here is the screenshot in Wireshark after using filter “arp”.

Packet number 1 is Arp Request and packet number 2 is Arp Reply. Now if we take information from capture and put it in diagram, it will look like this.
♦ ARP Request:
ARP Request is the first packet which is sent from the device which is looking for MAC address.
Here is the screenshot of ARP request packet with inside fields.

♦ ARP Reply:
ARP Reply is the packet which is sent from the device which has received the query in ARP request.
Here is the screenshot of ARP reply packet with inside fields.

Security concern related to ARP protocol is ARP spoofing.
Protocol standard for ARP is https://tools.ietf.org/html/rfc6747
♣ DHCP:
In simple sentence, DHCP is a process to get IP address from Server. There are mainly 4 packets exchanges in DHCP.
1. DHCP Discover
2. DHCP Offer
3. DHCP Request
4. DHCP Accept
Let’s see these 4 packets in simple diagram

DHCP Discover [Broadcast]
——————————————————————————————->
DHCP Offer [Broadcast]
<——————————————————————————————-
DHCP Request [Broadcast]
——————————————————————————————->
DHCP Accept [Broadcast]
<——————————————————————————————-
Note: These are mainly broadcast but these packets can be sent as unicast in some scenarios.
Let’s see these packets in Wireshark. We can use filter name as “bootp” to get DHCP packets

1. DHCP Discover:
Here is the screenshot to explain about important fields of DHCP discover packet.

From above packet we can understand that DHCP discover is a broadcast packet asking for IP address for client.
2. DHCP Offer:
Here is the screenshot to explain about important fields of DHCP offer packet.

As we can see DHCP offer packet has offered IP address, subnet mask, lease time and server informations like server IP, server domain name etc. Remember that client may receive multiple DHCP offer packets from multiple servers. But it’s client choice to send DHCP request packet to one server.
3. DHCP Request:
Here is the screenshot to explain about important fields of DHCP request packet.

Client can choose the server and send DHCP offer mentioning one DHCP server IP address. Also client asks for some parameter list from Server.
4. DHCP ACK:
Here is the screenshot to explain about important fields of DHCP ACK packet.

DHCP ACK packet is basically the Acknowledge packet from server with almost same information sent in packet DHCP offer.
Now the question comes what happens after 1 day. Client does DHCP renewal. For DHCP renewal there are 2 frame exchanges
1. DHCP Request: DHCP request packet fields are same as previous point 3 but here Client IP address field should be filled with client’s current IP [Example: 192.168.1.101 ] or we can say requested IP.
2. DHCP ACK: DHCP ACK us same as previous point 4.
But the difference is here DHCP Request is unicast packet because client knows its server. DHCP ACK is broadcast as usual.
See screenshot

Protocol standard for DHCP is https://tools.ietf.org/html/rfc2131
♣ TCP:
Transmission Control Protocol is a major protocol in Transport layer. Client and server have to exchange 3 packets to establish TCP connection. We can call it’s a TCP 3-way handshake.
TCP Connection:

Packet1: SYN is sent from Client—————————————>
<—————————–Packet2: SYN+ACK is sent from Server
Packet3: ACK is sent from Client—————————————>
Let’s see all three packets from Wireshark. We can use filter “tcp” to list out all tcp packets and the first 3 packets should be the 3-way hand shake packet. Have a look on below screenshot.

♦ SYN:
Here is the screenshot for SYN packet sent by client to server

Basically SYN packet is sent to share client’s capabilities to server.
SYN+ACK:
Now server share it’s capabilities to client through SYN+ACK packet. So this packet is acknowledgement of SYN packet and also sharing server’s capabilities.
Here is the screenshot

If we compare SYN and SYN+ACK packet we can see differences between client’s and server’s capabilities. These informations are useful when client and server shares TCP data packets.
♦ ACK:
Here is the screenshot of ACK packet

This packet is just the acknowledgement from client.
Now TCP connection is completed.
♣ TCP Teardown:
To discontinue existing TCP connection some packet exchanges occur between client and server. If client wants to terminate connection then client can send FIN packet and server sends ACK. Now if server also wants to terminate connection from its end then server sends FIN and gets ACK packet as reply. So, total 4 packets exchanges are happening for complete TCP connection close between client and server.

Packet1: FIN is sent from Client—————————————->
<——————————-——Packet2: ACK is sent from Server
<—————————————Packet3: FIN is sent from Server
Packet4: ACK is sent from Client—————————————>
Note: FIN packet is sent as FIN+ACK to indicate that this FIN packet also the ACK of any previous packet. Do not get confused.
There is no important information inside FIN and ACK packet as this indicates TCP connection termination.
Here is the screenshot for FIN packet

In reply to FIN, only ACK packet is sent as an acknowledgement. Here is the screenshot of ACK packet.

Protocol standard for TCP is https://tools.ietf.org/html/rfc793
Some security threats related to TCP is TCP half open, TCP full scan, TCP Null scan etc.
♣ Conclusions:
From the above article we got basic idea about ARP, DHCP, TCP protocol and their important fields in Wireshark. For deep dive we can go through the shared RFC link.
♥♥If you have any doubts or query please let me know in comment section or send mail at feedback@wifisharks.com.♥♥

Sandy
Hi Bamdeb , what might be the reasons behind ping is not working even though ARP Resolution Successfully Completed .
For DHCP IP Renewal , Will Client uses the same Txion identifier which was used in the process of getting the ip initially ?
Bamdeb
Hi Sandy,
There may be various reasons but i am not able tell exact reason. Will share if i get any idea on this.
If you can share more details on scenario and sniffer captuer, i can try,
There may be minor mistakes like
1. Please check set up
2. Ip address is correct?
3. Try pinging from other side
etc etc
Regarding,
DHCP renewal ==> I do not know this exactly. Will explore and share.
Nisha
Nice page